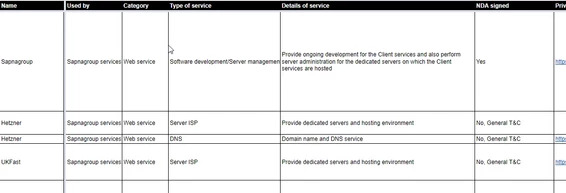
Maintaining the supplier/processor list is one of the key security requirements for any orgranisation and is the list of all the suppliers and/or processor (or sub-processors) who are involved in a project or process. This means if your processor has a sub-processor ideally that sub-processor also needs to be in this list.
This document should ideally contain
- Basic contact details
- Exact relationship and what function they have in the process
- Security steps undertaken, like NDA, security policy, privacy policy etc
- Contracts signed
- Exact data they have exposure
- Medium used to transfer the said data
- Countries the data is exposed for each supplier and all its sub-processor.
Having this list helps as it
- Forms the basis for the data flow diagram which is also an important security documentation
- Gives you a good overview of who and what data is being shared
- Helps allow you in emergency situations to inform your supplier and sub processor
- Forms the basis of many security document requirements
- Helps easy review every 6 months, if a supplier is no longer used, one can easily see what data was exposed, and accordingly close those channels
Helping organisations build their supplier list along with a range of other important documents forms the foundation of our security audit. Please contact us if you have any questions.