-
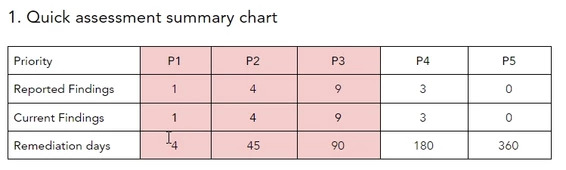
OS command injection in latest ethical hack findings
In the latest ethical hack conducted by our security team on a security related service, we managed to find a very interesting OS command injection finding which is Priority level 1.In the latest ethical hack conducted by our security team on a security related service, we managed to find a very interesting OS command injection…
-
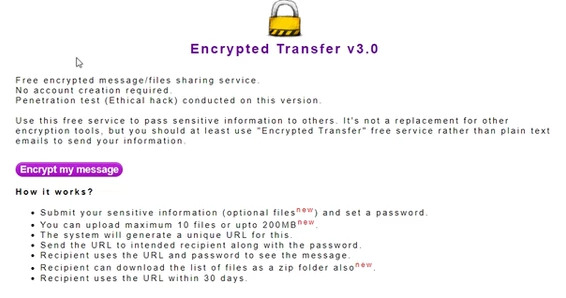
encryptedtransfer.com is now more secure and allows file transfers
The idea for our free online tool www.encryptedtransfer.com for safely passing messages started more than 8 years back. It has been popular with our team and clients using it very regularly to send access details and passwords. Since we have started the service more than 15,000 messages were exchanged securely using the best industry standards.…
-
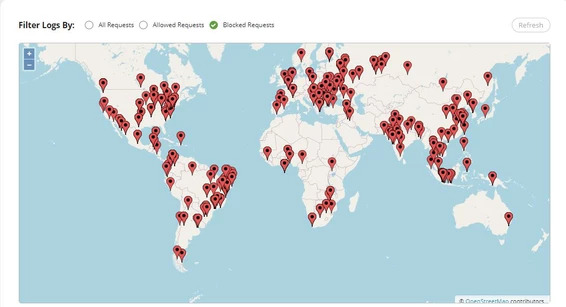
DDOS attack and possible solutions
Recently we had a DDOS attack on a systems we handle for one of our client. The image above shows the different places from where the attacks were happening. But before we get into all that, a little bit about DDOS means: Denial of Service is a form of attack which takes advantage of the…
-

Top 5: Server Administration recommendations
Our top 5 recommendations for server administrators are Always use the latest version of the OS and the software and ensure your software has active support. Install and use only services you need. Left over services which you dont need can often lead to open doors which are not being managed as you are not…
-

Infrastructure vulnerability test conducted
Recently an infrastructure vulnerability test was conducted on one of numerous setups managed by us. For this test the live environment was replicated with a dedicated web server and database server. The hardware firewall remained the same (for both production and test). The Principle Security Concerns (“PSCs”) that were addressed via testing activities were as…
-
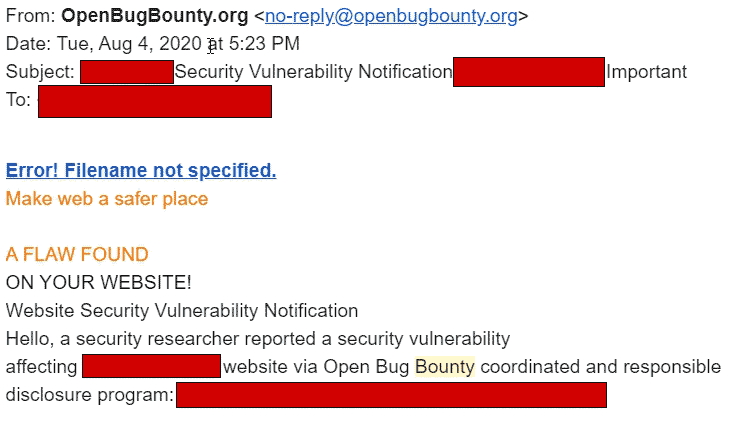
bugbounty email?
If you happen to receive an email similar to the one above, don’t panic. The bug bounty programs including the open bugbounty is a system designed to make the public accessible systems safe. Rather than a hacker misusing the exploit, bug bounty hackers warn you of a possible exploit, and give you enough time to…
-

Internal policy and process/documentation update
For the past few months we have been busy reviewing our policy and processes Work from Home policy (This was done early on when WFH hit us. Luckily our office had done a few practice runs with half to staff working from home few weeks before ensuring a smooth transition) Updating our encrypted transfer system…
-

250 million customer records compromised by Microsoft. Mis-configured database.
For more than 3 weeks, 5 five Elasticsearch servers of Microsoft left 250 million customer support records publicly exposed. The misconfiguration was done on 5th December and was reported to Microsoft on 31st December after which all 5 servers were secured within 24 hours. https://www.scmagazine.com/home/security-news/database-security/microsoft-database-misconfiguration-exposes-250m-customer-support-records/
-

15 “Priority 1” vulnerabilities detected by our team
From SQL and XSS injections, 3rd party vulnerabilities, file upload issues to password policy we ran a comprehensive penetration test and found a range of vulnerabilities for this client’s portal. With 15 “Priority 1” and a number of other vulnerabilities our team did a great job making a detailed examination and report. “Priority 1” vulnerabilities…