Around 8 months back we conducted a non-intrusive security audit for an accounting backend application which involved us going through their system and making data classification matrix, supplier/processor list, data flow, network diagrams and conducting fact finding in various areas like application security, data security, infrastructure, access management, monitoring/logging, and organisational policy.
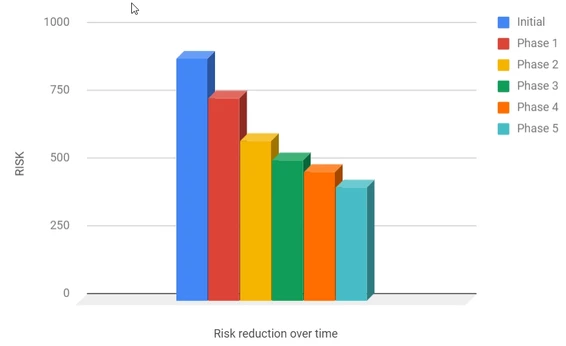
At the end of the entire exercise we generated a risk register which helped us keep track and prioritize items. 25 risk items (with a total score of 472 risk points) were picked up and closed from this pool over 5 phases, which helped us keep smaller goals and not overwhelm the client and developers. This phased approach is important as it also helped us focusing on the right issues and split costs over a period of time.
The chart above shows the initial total risk (sum of all risk scores) and the subsequent aggregate risk value after we completed a risk reduction phase. While the chart above may show significant risk items still pending these are low risk items which have been compensated with alternative fixes and will continue to be part of the risk register for future evaluation. No application has zero risk, as it’s impossible to reach that state. Even NASA will have a risk register with risk items – so don’t let the last bar fool you.
For now we are happy to close our evaluation for this year.
You can download our scope document to know a little bit more about our process.