Risk management while sounding threatening and complicated is really very simple; you need to identify/list all the risks, prioritise them, and then find effective and economical ways to reduce these risks. This is also an important GDPR requirement. The steps needed to follow are
- Identifying risks: find out what could cause harm. A good group discussion, conducting internal and external audits are a good start. The process should be on-going whenever anyone identifies a risk they need to report it. The risk scope should not be limited and should cater to organisation, people, environment, assets including system, policies and procedures, software, services, 3rd party etc. The best way to do this is to make a risk register which contains all details of the risk, including probability, impact, and risk value as explained below.
- Assessing threats: A risk register is a list of all risks which helps you focus on the core issues with the help of 2 factors probability and impact. The likely fields you need for risk register are
- Type/Category (Could be a department, process etc)
- Owner (the one who is assigned to manage this risk)
- Description
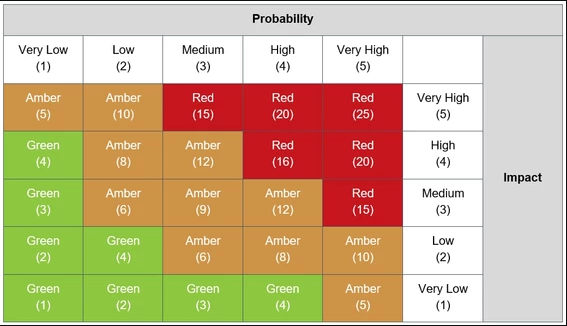
- Probability (Understand the probability/likelihood of a risk and how serious it could be. Probability of a risk occurring is given a rating from 0-5 from 0 being very low probability, and 5 being very high probability.)
- Impact (Similarly, risk-impact the risk would have if exploited is given the same rating from 0-5 from very low impact or consequences to very high.)
- Risk rating (Risk is then calculated as a product of these 2 numbers, so with risk-probability of 2 and risk-impact of 3 the Risk value is 2×3=6.)
- Existing mitigation (What existing compensating factors you have which lower the risk)
- Next Plans (what are the agreed next steps to lower or accept this risk)
- Next review date (when to discuss this risk again)
- Status (Open, Closed, Accepted risk etc).
If a risk is accepted then you also need to maintain an exception policy where risk exceptions are maintained.Each risk is thus given a value. This helps in evaluating which risks need to be given higher priority as can be seen in the Risk traffic light scoring. 0-4 risk value: are low risk issues, and hence have low priority5-12 risk value: are medium risk issues, with medium priority15-25 risk value are high risk issues, with high priority. These items have the maximum security and financial implications.
- Controlling risks: Taking action to anticipate or manage them; implement the most effective control measure that is reasonably practicable and economical in the circumstances. Sometimes a simple remediation will help lower the risk immediately and is a much better option then fixing the risk head-on which might be expensive, time consuming and get delayed. Assign risks to an individual who will lead to close this risk and set a deadline.
- Reviewing risks: Monitoring them and reviewing progress in order to establish whether or not any further action may be necessary. Management approval is also required here. Organisations should review risks at least every 6 months.
Ideally you need a central system which manages other security bits including risk management however your current task monitoring system can be used, or in the worst case a simple excel sheet. Please take care to protect the sheet with the password as you don’t want to inform everyone about the potential risks your organisation might have.
Contact us at [email protected] if you need help managing risk in your organisation or have queries on the same.